Publications
publications by categories in reversed chronological order. generated by jekyll-scholar.
2025
-
 VerificAgent: Domain-Specific Memory Verification for Scalable Oversight of Aligned Computer-Use AgentsThong Q. Nguyen , Shubhang Desai , Raja Hasnain Anwar , and 3 more authors2025
VerificAgent: Domain-Specific Memory Verification for Scalable Oversight of Aligned Computer-Use AgentsThong Q. Nguyen , Shubhang Desai , Raja Hasnain Anwar , and 3 more authors2025@misc{nguyen2025verificagentdomainspecificmemoryverification, title = {VerificAgent: Domain-Specific Memory Verification for Scalable Oversight of Aligned Computer-Use Agents}, author = {Nguyen, Thong Q. and Desai, Shubhang and Anwar, Raja Hasnain and Shaik, Firoz and Suryanarayanan, Vishwas and Chowdhary, Vishal}, year = {2025}, eprint = {2506.02539}, archiveprefix = {arXiv}, primaryclass = {cs.LG}, url = {https://arxiv.org/abs/2506.02539}, } -
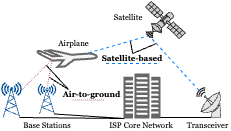 Cloud Nine Connectivity: Security Analysis of In-Flight Wi-Fi Paywall SystemsAbdullah Al Ishtiaq , Raja Hasnain Anwar , Yasra Chandio , and 3 more authorsIn 18th ACM Conference on Security and Privacy in Wireless and Mobile Networks , 2025* First two authors contributed equally.
Cloud Nine Connectivity: Security Analysis of In-Flight Wi-Fi Paywall SystemsAbdullah Al Ishtiaq , Raja Hasnain Anwar , Yasra Chandio , and 3 more authorsIn 18th ACM Conference on Security and Privacy in Wireless and Mobile Networks , 2025* First two authors contributed equally.In-flight Wi-Fi provides high-speed Internet connectivity to travelers at 30,000 feet at premium fees. In this paper, we present the first systematic study of the architecture and security policies of in-flight Wi-Fi paywall systems using network tomography analysis. We discover that attackers can exploit the inherent architectural shortcomings of airborne networks to create covert channels and conceal data packets within certain ”always-allowed” traffic for free Internet access. Moreover, broken device authentication policies in these systems allow unlimited complimentary Internet connectivity. Finally, insecure ARP policies allow attackers to steal paid users’ bandwidth to access the free Internet even faster. We validate these issues in practice over two major in-flight Wi-Fi providers using common protocols, e.g., UDP, DNS, etc. We also find that the root causes of these issues stem from different design choices in the architectures of these systems and propose countermeasures to address these flaws and prevent similar attacks.
@inproceedings{10.1145/3734477.3734713, author = {Ishtiaq, Abdullah Al and Anwar, Raja Hasnain and Chandio, Yasra and Anwar, Fatima Muhammad and Hussain, Syed Rafiul and Raza, Muhammad Taqi}, title = {Cloud Nine Connectivity: Security Analysis of In-Flight Wi-Fi Paywall Systems}, year = {2025}, isbn = {9798400715303}, publisher = {Association for Computing Machinery}, address = {New York, NY, USA}, url = {https://doi.org/10.1145/3734477.3734713}, doi = {10.1145/3734477.3734713}, booktitle = {18th ACM Conference on Security and Privacy in Wireless and Mobile Networks}, pages = {76–87}, numpages = {12}, keywords = {in-flight wi-fi, paywall bypass, paywall systems}, location = {Arlington, VA, USA}, series = {WiSec 2025}, note = {* First two authors contributed equally.} }
2024
-
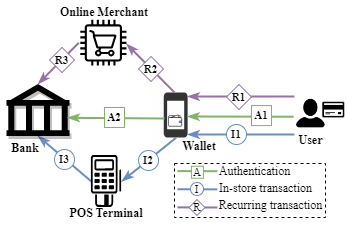 In Wallet We Trust: Bypassing the Digital Wallets Payment Security for Free ShoppingRaja Hasnain Anwar , Syed Rafiul Hussain , and Muhammad Taqi RazaIn USENIX Security Symposium , 2024
In Wallet We Trust: Bypassing the Digital Wallets Payment Security for Free ShoppingRaja Hasnain Anwar , Syed Rafiul Hussain , and Muhammad Taqi RazaIn USENIX Security Symposium , 2024Digital wallets are a new form of payment technology that provides a secure and convenient way of making contactless payments through smart devices. In this paper, we study the security of financial transactions made through digital wallets, focusing on the authentication, authorization, and access control security functions. We find that the digital payment ecosystem supports the decentralized authority delegation which is susceptible to a number of attacks. First, an attacker adds the victim’s bank card into their (attacker’s) wallet by exploiting the authentication method agreement procedure between the wallet and the bank. Second, they exploit the unconditional trust between the wallet and the bank, and bypass the payment authorization. Third, they create a trap door through different payment types and violate the access control policy for the payments. The implications of these attacks are of a serious nature where the attacker can make purchases of arbitrary amounts by using the victim’s bank card, despite these cards being locked and reported to the bank as stolen by the victim. We validate these findings in practice over major US banks (notably Chase, AMEX, Bank of America, and others) and three digital wallet apps (ApplePay, GPay, and PayPal).
@inproceedings{anwar2023wallet, title = {In Wallet We Trust: Bypassing the Digital Wallets Payment Security for Free Shopping}, author = {Anwar, Raja Hasnain and Hussain, Syed Rafiul and Raza, Muhammad Taqi}, booktitle = {USENIX Security Symposium}, pages = {541--558}, year = {2024}, url = {https://www.usenix.org/conference/usenixsecurity24/presentation/anwar}, } -
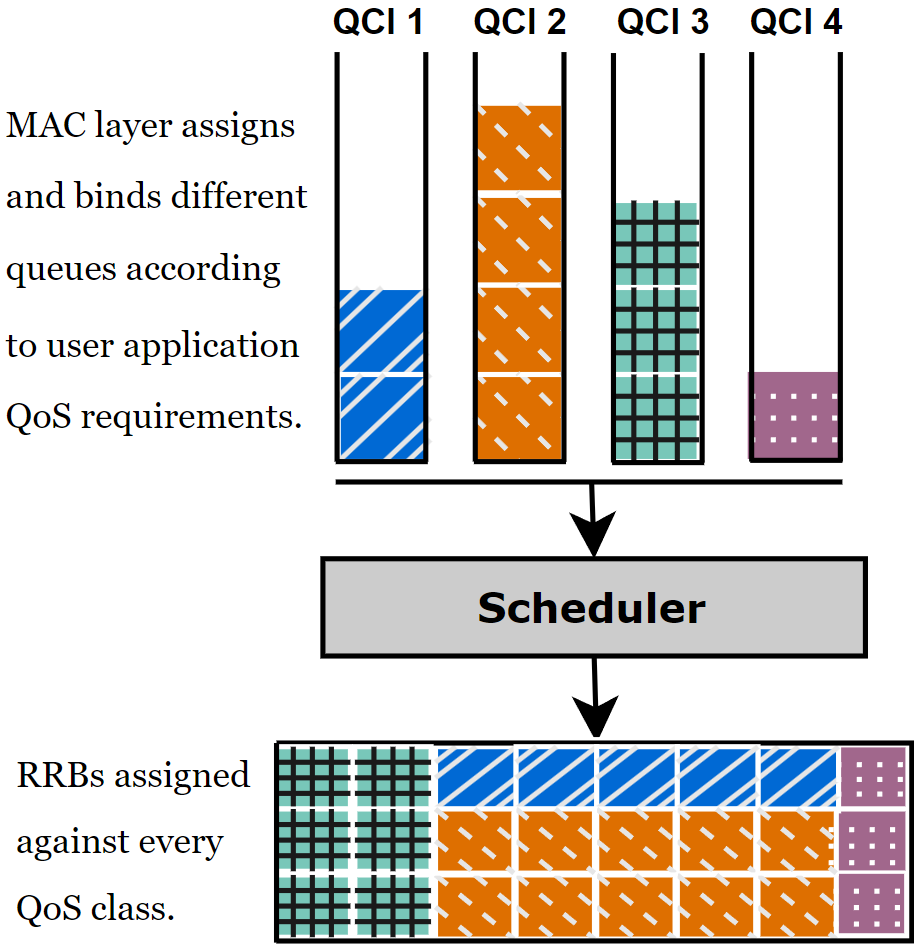 Characterizing Encrypted Application Traffic through Cellular Radio Interface ProtocolMd Ruman Islam , Raja Hasnain Anwar , Spyridon Mastorakis , and 1 more authorIn IEEE International Conference on Mobile Ad-Hoc and Smart Systems (MASS) , 2024
Characterizing Encrypted Application Traffic through Cellular Radio Interface ProtocolMd Ruman Islam , Raja Hasnain Anwar , Spyridon Mastorakis , and 1 more authorIn IEEE International Conference on Mobile Ad-Hoc and Smart Systems (MASS) , 2024Modern applications are end-to-end encrypted to prevent data from being read or secretly modified. 5G tech nology provides ubiquitous access to these applications without compromising the application-specific performance and latency goals. In this paper, we empirically demonstrate that 5G radio communication becomes the side channel to precisely infer the user’s applications in real-time. The key idea lies in observing the 5G physical and MAC layer interactions over time that reveal the application’s behavior. The MAC layer receives the data from the application and requests the network to assign the radio resource blocks. The network assigns the radio resources as per application requirements, such as priority, Quality of Service (QoS) needs, amount of data to be transmitted, and buffer size. The adversary can passively observe the radio resources to fingerprint the applications. We empirically demonstrate this attack by considering four different categories of applications: online shopping, voice/video conferencing, video streaming, and Over-The-Top (OTT) media platforms. Finally, we have also demonstrated that an attacker can differentiate various types of applications in real-time within each category.
@inproceedings{islam2024characterizing, title = {Characterizing Encrypted Application Traffic through Cellular Radio Interface Protocol}, author = {Islam, Md Ruman and Anwar, Raja Hasnain and Mastorakis, Spyridon and Raza, Muhammad Taqi}, booktitle = {IEEE International Conference on Mobile Ad-Hoc and Smart Systems (MASS)}, year = {2024}, url = {https://arxiv.org/pdf/2407.07361}, }
2023
-
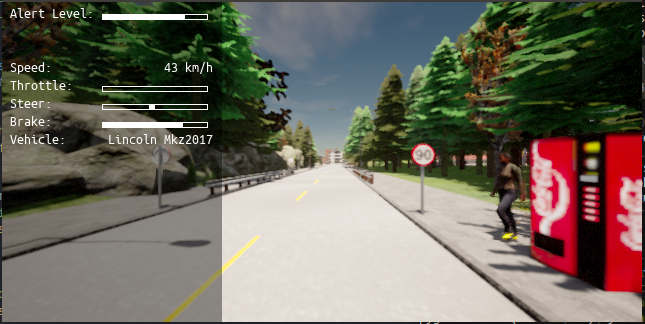 Redefining the Driver’s Attention Gauge in Semi-Autonomous VehiclesRaja Hasnain Anwar , Fatima Muhammad Anwar , Muhammad Kumail Haider , and 2 more authorsIn Proceedings of the Int’l ACM Conference on Modeling Analysis and Simulation of Wireless and Mobile Systems (MSWiM) , 2023
Redefining the Driver’s Attention Gauge in Semi-Autonomous VehiclesRaja Hasnain Anwar , Fatima Muhammad Anwar , Muhammad Kumail Haider , and 2 more authorsIn Proceedings of the Int’l ACM Conference on Modeling Analysis and Simulation of Wireless and Mobile Systems (MSWiM) , 2023Driver distraction caused by over-reliance on automotive technology is one of the leading causes of accidents in semi-autonomous vehicles. Existing driver’s attention-gauging approaches are intrusive and as such emphasize constant driver engagement. In case of an urgent traffic event, they fail to measure the event’s criticality and subsequently generate timely alerts. In this paper, we re-position the driver’s attention-gauging approach as a way to improve the driver’s situational awareness during critical situations. We exploit how a vehicle captures its surroundings information to convert an automotive decision into defining the criticality and timeliness of an alert. For this, we identify the relationship between the traffic event, the type of automotive sensing technologies, and its processing resources to capture that event to design the driver’s attention gauge. We evaluate the timeliness of alerts for different traffic scenarios over a prototype built using NVIDIA Jetson Xavier AGX and Carla. Our results show that we can improve the timeliness of an alert by up to 75x as compared to existing state-of-the-art approaches, while also providing feedback on its criticality.
@inproceedings{anwar2023redefining, title = {Redefining the Driver's Attention Gauge in Semi-Autonomous Vehicles}, author = {Anwar, Raja Hasnain and Anwar, Fatima Muhammad and Haider, Muhammad Kumail and Efrat, Alon and Raza, Muhammad Taqi}, booktitle = {Proceedings of the Int'l ACM Conference on Modeling Analysis and Simulation of Wireless and Mobile Systems (MSWiM)}, pages = {307--311}, year = {2023}, url = {https://dl.acm.org/doi/10.1145/3616388.3617544}, } -
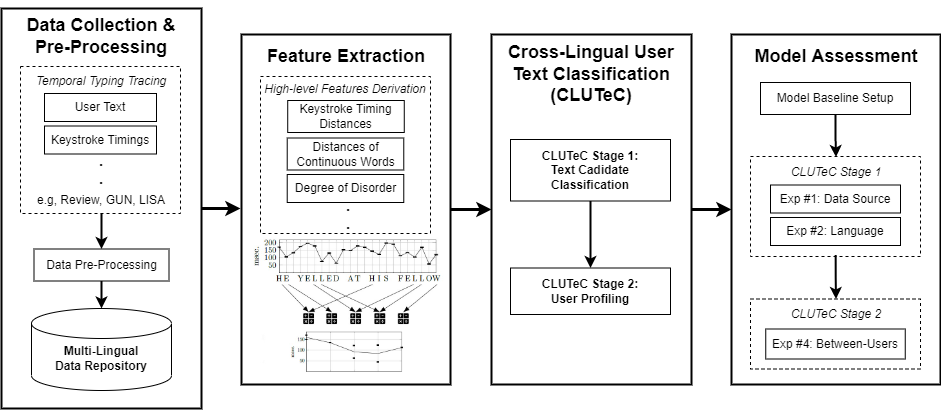 Detecting Privacy Threats with Machine Learning: A Design Framework for Identifying Side-Channel Risks of Illegitimate User ProfilingRaja Hasnain Anwar , Yi Zoe Zou , and Muhammad Taqi RazaIn Proceedings of the Americas Conference on Information Systems (AMCIS) , 2023
Detecting Privacy Threats with Machine Learning: A Design Framework for Identifying Side-Channel Risks of Illegitimate User ProfilingRaja Hasnain Anwar , Yi Zoe Zou , and Muhammad Taqi RazaIn Proceedings of the Americas Conference on Information Systems (AMCIS) , 2023Privacy leakage has become prevalent and severe with the increasing adoption of the internet of things (IoT), artificial intelligence (AI), and blockchain technologies. Such data-intensive systems are vulnerable to side-channel attacks in which hackers can extract sensitive information from a digital device without actively manipulating the target system. Nevertheless, there is a scarcity of IS research on how businesses can effectively detect and safeguard against side-channel attacks. This study adopts the design science paradigm and lays the groundwork for systematic inquiry into the assessment of privacy risks related to side-channels. In this paper, we a) highlight the privacy threats posed by side-channel attacks, b) propose a machine learning-driven design framework to identify side-channel privacy risks, and c) contribute to the literature on privacy analytics using machine learning techniques. We demonstrate a use case of the proposed framework with a text classification model that uses keystroke timings as side-channel.
@inproceedings{anwar2023detecting, title = {Detecting Privacy Threats with Machine Learning: A Design Framework for Identifying Side-Channel Risks of Illegitimate User Profiling}, author = {Anwar, Raja Hasnain and Zou, Yi Zoe and Raza, Muhammad Taqi}, booktitle = {Proceedings of the Americas Conference on Information Systems (AMCIS)}, year = {2023}, url = {https://aisel.aisnet.org/amcis2023/sig_sec/sig_sec/7/}, }
2021
- Keeping eyes on the road: the role of situated IS delegation in influencing drivers’ situational awarenessRaja Hasnain Anwar , Taqi Raza , and Yi Zoe ZouIn International Conference on Information Systems (ICIS) TREOs , 2021
@inproceedings{anwar2021keeping, title = {Keeping eyes on the road: the role of situated IS delegation in influencing drivers' situational awareness}, author = {Anwar, Raja Hasnain and Raza, Taqi and Zou, Yi Zoe}, booktitle = {International Conference on Information Systems (ICIS) TREOs}, year = {2021} }